The metaverse is quickly turning into a key part of how people interact online, mixing lifelike digital spaces with everyday activities, hanging out, shopping, working, or playing games. Instead of just logging in, folks now build custom avatars to move around, join gatherings, or buy digital items such as plots of land or NFTs using blockchain networks. Since these online personas carry more data and worth over time, keeping them safe becomes harder and way riskier if ignored. Staying secure in this space isn’t optional anymore, it’s basic survival for regular users and companies both.
This blog looks into new dangers popping up in the metaverse, digs into tech hurdles plus human habits affecting digital ID safety, while showing how companies such as Codearies support building online spaces that are safe, reliable, yet simple to use.
Understanding Virtual Identities in the Metaverse
A virtual identity works like an online version of you built using avatars, user handles, digital items, past actions, how others see you, also who you know. These profiles usually tie into wallet apps on blockchains that hold coins, unique digital collectibles, or permissions when jumping into metaverse spaces.
Metaverse IDs aren’t like regular online profiles, they often carry real value, mixing personal info, digital items, or even habits across open networks. Keeping them safe means new kinds of protection, not just typical antivirus stuff.
Unique Security Challenges in Metaverse Virtual Identities
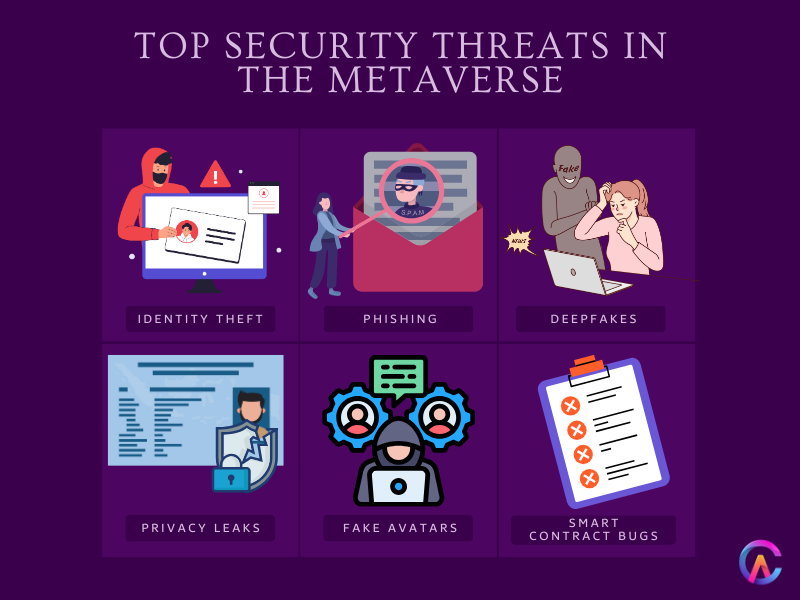
1. Identity Theft and Account Takeover
Hackers go after wallet passwords, secret codes, or account logins, snatching digital coins, unique assets, or whole online properties. Once money moves on blockchain, it sticks, no way back if scammers pull off a theft.
2. Phishing and Social Engineering
Fraudsters use sneakier tricks now, getting people to hand over private info by pretending fake apps are real, like wallets or updates for the metaverse. With more chatting and connecting online, chances for attacks grow too.
3. Privacy Leakage and Data Aggregation
Virtual IDs collect loads of actions and purchases, building records that might get tracked or sold without permission. If settings are wrong or rules too weak, people could face sneaky monitoring, this chips away confidence.
4. Fake Identities and Deepfakes
AI made faces plus fake videos make it easier to pretend being someone else, steal identities, or ruin reputations. People might talk to these false profiles without realizing, opening doors to tricks or influence.
5. Cross Platform Identity Management Complexity
People usually split their online personas across different virtual worlds, which run on separate networks without clear rules for safe logins or permissions. This scattered setup opens more doors for hacks or stolen data.
6. Smart Contract Vulnerabilities
Smart contracts that handle ID checks, who owns tokens, or permissions might have flaws or get hacked, putting real ownership at risk while users lose faith in blockchain systems.
Technical Approaches to Securing Virtual Identities
Decentralized Identity (DID) Protocols
Emerging decentralized identity standards provide users self sovereign control over verifiable credentials enabling privacy preserving and interoperable identity claims across metaverse ecosystems.
Multi Factor and Biometric Authentication
Enhanced authentication methods protect wallet access and identity controls combining hardware keys, biometric recognition, and adaptive risk checks to reduce account compromise.
Hardware Wallets and Cold Storage
Cold wallets keep private keys off the internet, so hackers can’t reach them, yet they let you sign transactions safely, working smoothly with apps that support them.
Encryption and Zero Knowledge Proofs
End to end encryption keeps info safe while moving or sitting on servers, while zero knowledge proofs check who you are without showing private details, which cuts down privacy dangers.
Continuous Auditing and Smart Contract Formal Verification
Outside checks or step by step validations reduce weak spots in digital agreements that handle IDs and property on virtual world apps.
AI Driven Threat Detection
Machine learning checks for odd actions, while also spotting sketchy data flows or phishing tricks, helping teams react fast.
Best Practices for Users
- Go for trusted wallets or try reliable apps
- Turn on two step verification also keep your recovery codes safe
- Keep your private keys safe, never show them around. Also, don’t display QR codes where others can scan them
- Check where stuff’s coming from before you download anything or tap on URLs
- Handle permissions carefully, give only what’s truly needed
- Keep your apps fresh, fix weak spots before they’re exploited

The Role of Platforms and Businesses in Securing Virtual Identities
Metaverse creators must build systems that protect users while focusing on their needs. That means thinking about safety first, yet also making sure personal info stays private
- Clear rules about data use, people agree freely systems built on trust not forced choices, everyone stays informed
- Friendly ways to get your ID back safely so you won’t lose access easily, because protection matters when things go wrong
- Fraud checks come included, while issues can move up through help channels
- Local workshops about new dangers
- Working alongside cyber pros or officials to shape common rules
How Codearies Helps Protect Virtual Identities in the Metaverse
With Codearies, customers get support creating safe online spaces, flexible ones that handle growth while keeping digital identities protected over time. Our focus? Making virtual experiences smooth without compromising privacy or performance down the line.
Our services include
- Decentralized Identity Solutions Designing and implementing DID standards for seamless and privacy preserving identity management
- Smart contract audits plus building solid setups for ID handling, tokens, access rules, checked by outside experts
- Multi Factor and Biometric Authentication Integration Enhancing wallet and platform security with advanced real time user verification tools
- Secure messaging setups that keep info private from start to finish, meeting rules while letting users control their own data
- AI tools spot dangers fast. Using smart software that learns on its own. This helps catch problems early in virtual worlds. Systems react quick when trouble hits. Protection fits weird new risks online. Not just old methods with extra tech slapped on
- User Onboarding Education Creating intuitive onboarding flows and security awareness training to empower users against social engineering
- Compliance Consulting Aligning platforms with evolving metaverse regulations and emerging identity governance frameworks
Teaming up with Codearies lets your metaverse venture deliver safe, reliable IDs, boosting user protection while encouraging lasting involvement through solid trust.
Frequently Asked Questions
Q1 What makes metaverse identity security different from traditional web security?
The mix of tokenized assets on a network, unchangeable records, also shared virtual experiences brings new dangers that need unique digital ID systems built on distributed tech
Q2 Can Codearies help secure existing blockchain wallet integrations?
Yes, we boost your wallet’s safety using two step checks, support for physical wallets, also built in scam link warnings
Q3 How do decentralized identity protocols enhance privacy?
DIDs let people choose what info to share with sites, cutting down on oversharing private details
Q4 What is the role of AI in metaverse security?
AI spots fraud clues fast like weird logins or scam messages, so defenses kick in before harm hits
Q5 How does Codearies assist with user education on identity risks?
We create step by step guides that help users learn fast, while blending quick walkthroughs into apps, so people stay alert against scams using smooth, built in lessons instead of separate courses
For business inquiries or further information, please contact us at