Did you know that 45% of Americans have had their personal information compromised by a data breach in the last five years? Also, 86% of data breaches involve stolen credentials. How identities are managed today is deeply flawed. From usernames and passwords to third-party authentication systems, significant weaknesses leave individuals and businesses vulnerable. Centralized databases hold massive amounts of personal data, making them prime targets for hackers. Even with advanced encryption techniques, these centralized systems are prone to breaches, exposing millions of people to identity theft or fraud. The complexity of managing multiple identities across different platforms also creates inefficiencies and a lack of user control. The current digital identity system is in dire need of an overhaul, and that’s where AI-powered blockchain solutions come in.
Key Elements of Digital Identity
Digital Identity encompasses various essential components. Here’s a breakdown of the key elements:
Personal Identifiers
Unique identifiers are specific numbers or codes that set individuals apart, such as national ID numbers (like India’s Aadhaar), driver’s license numbers, and passport IDs. Biometric data refers to distinctive physical characteristics, including fingerprints, facial recognition, and iris patterns, for verifying Identity.
Credentials
Passwords and PINs are secret codes that grant access to online accounts. Security tokens are devices or apps that generate one-time authentication codes. Digital certificates are electronic documents that verify individuals’ or organizations’ identities.
Data Security
Encryption is the method of converting data into a coded format to prevent unauthorized access. Authentication verifies a user’s Identity before granting system access, while authorization determines their permissions. Access control involves measures to restrict access to sensitive information, and data privacy focuses on protecting personal information from unauthorized use or disclosure.The integration of these components is vital for creating a secure and trustworthy digital identity. For example, personal identifiers facilitate user authentication, while credentials (like passwords) add another layer of security. Data security measures are crucial in protecting sensitive information linked to an individual’s Identity.
Blockchain and Its Impact on Digital Identity
Blockchain technology is increasingly recognized as a viable solution for decentralized identity management, offering distinct advantages over conventional centralized systems.
How Blockchain Transforms Identity Management
Blockchain utilizes a distributed ledger system, removing centralized control and reducing the risk of single points of failure and data breaches. Once information is recorded on the blockchain, it remains immutable, ensuring the integrity of identity data. Transactions are transparent, allowing all participants to verify identity claims, which builds trust. Individuals retain control over their identity data, deciding who can access it and how it is used. Blockchain-based identity solutions can connect seamlessly, enabling users to share their information across different platforms. For example, a user could use their blockchain-based ID to access services across various applications without creating separate accounts for each.
Key Advantages of Blockchain for Digital Identity
- Enhanced Security: The decentralized blockchain structure significantly lowers the risk of data breaches and identity theft.
- Increased Trust: The transparency and immutability of blockchain enhance user confidence in the authenticity of identity information.
- Greater User Control: Individuals have more authority over their identity data, empowering them to make informed choices about its use.
- Reduced Dependence on Central Authorities: By eliminating the need for central identity information management, blockchain mitigates the risks of censorship and discrimination.
Enhancing Digital Identity Security with AI
Artificial Intelligence (AI) is revolutionizing digital identity security by analyzing data, recognizing patterns, and adapting to emerging threats. It is an essential ally in safeguarding personal information.
Key Contributions of AI
Advanced Threat Detection: AI can spot unusual user behaviours and network anomalies, detect phishing attempts, and block malware before it causes harm.Biometric Authentication: AI enhances the accuracy of biometric methods like facial recognition and fingerprint scanning while differentiating between live users and spoofed data.Behavioral Analytics: By monitoring user activity, AI can identify unauthorized access and assess risks in real-time.Adaptive Authentication: AI adjusts authentication methods based on context, requiring additional steps for high-risk transactions or suspicious activities.Fraud Prevention: AI instantly detects fraudulent patterns in transactions and assigns risk scores to prioritize further investigation.Continuous Learning: AI adapts to new threats through machine learning, helping organizations stay ahead of cybercriminals.
The Importance of Privacy in Digital Identity: Safeguarding User Privacy with Blockchain and AI
Imagine having your personal information stolen, leading to identity theft or financial fraud. Scary, right? Unfortunately, unauthorized access to our data can result in severe consequences. Beyond theft, sharing sensitive information can expose individuals to discrimination based on race, gender, or health status. Plus, with the rise of surveillance, excessive data collection threatens our freedom and privacy.
Blockchain and Privacy
Blockchain technology shines as a guardian of privacy in digital Identity. Deciding data across a network minimizes the risk of single points of failure, making data breaches less likely. Once recorded, data on a blockchain is nearly impossible to alter, ensuring that personal information remains intact. Users can engage in the digital realm through pseudonyms, keeping their real identities under wraps and having complete control over who accesses their information—empowering them with consent-based sharing.
AI and Privacy
Artificial Intelligence is also a key player in the privacy game. It can anonymize data, making it nearly impossible to trace back to individuals. Techniques like differential privacy introduce a layer of noise to datasets, protecting individual identities while allowing for valuable analysis. Plus, privacy-preserving machine learning enables algorithms to work with data without exposing sensitive information, adding another layer of security.
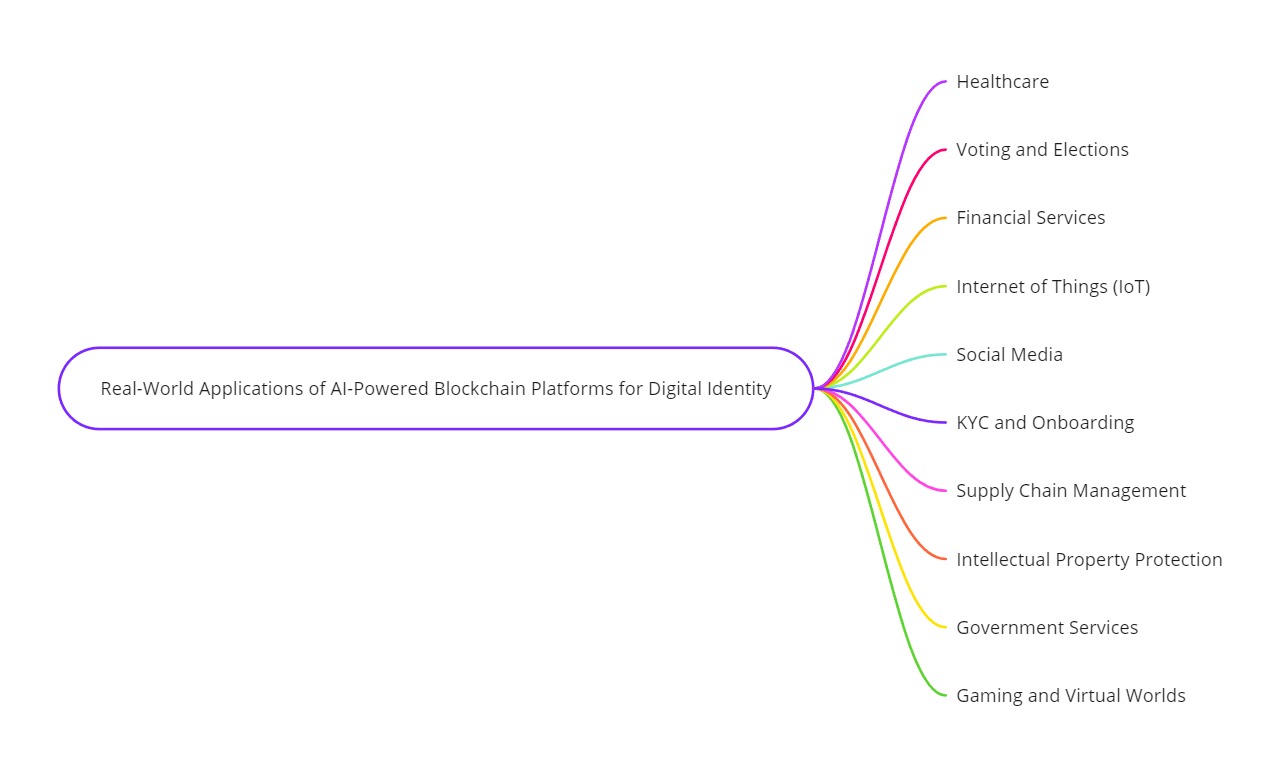
Use Cases of AI-Enhanced Blockchain in Identity Management
The fusion of artificial intelligence (AI) and blockchain technology opens up exciting possibilities for identity management across various sectors. Here are some dynamic use cases that showcase their potential:
Supply Chain Transparency and Authenticity
- Product Provenance: Imagine being able to trace the journey of a product from its source to your hands. AI can analyze blockchain data to ensure authenticity and help combat counterfeiting, giving consumers peace of mind about what they buy.
- Ethical Sourcing: AI can identify suppliers who follow ethical and sustainable practices, fostering trust and responsibility in purchasing decisions.
Healthcare Records Management
- Secure Data Sharing: Blockchain offers a secure way to store and share patient health records, making it easier for healthcare providers to collaborate without compromising privacy.
- Data Privacy: With AI’s ability to anonymize sensitive information, patient data can be protected while still allowing valuable insights for research and treatment.
Voting Systems
- Fraud Prevention: Blockchain provides an unchangeable record of votes, making election tampering nearly impossible. This could revolutionize how we think about electoral integrity.
- Enhanced Voter Participation: AI can simplify voter registration and verification, breaking down barriers and encouraging greater civic engagement.
Intellectual Property Protection
- Digital Rights Management: Blockchain can track ownership and usage rights for digital assets like music, art, and software, ensuring creators are credited for their work.
- Anti-Piracy Measures: AI can detect unauthorized distribution of copyrighted material, helping protect artists and innovators.
Financial Services
- Identity Verification: AI can quickly analyze biometric data and other identifiers, streamlining customer authentication and enhancing security.
- Fraud Detection: By spotting unusual spending patterns, AI can effectively flag potential fraud, protecting consumers and businesses.
Government Identity Management
- Citizen Services: Blockchain can transform how governments verify identities, providing a secure and efficient way to access services.
- Combating Corruption: Transparency provided by blockchain can help reduce corruption, promoting accountability in public service.
Social Media Platforms
- Decentralized Identity: Users can take control of their identity data on a blockchain, reducing reliance on centralized platforms and enhancing personal agency.
- Privacy Safeguards: AI is critical in protecting user privacy by identifying and preventing potential data breaches.
Internet of Things (IoT) Security
- Device Authentication: Blockchain can verify the authenticity of IoT devices, preventing unauthorized access and ensuring a secure network.
- Data Integrity: AI analyzes data from IoT devices to detect anomalies, ensuring the accuracy and reliability of information.
These examples illustrate how the powerful combination of AI and blockchain reshapes identity management and security.
Interoperability of Digital Identity Systems
Interoperability in digital identity systems is essential for seamless communication and data sharing across platforms, enhancing user convenience and security. Key approaches to achieving this include adopting open standards, creating identity federations for single-sign-on access, utilizing blockchain for secure data sharing, and leveraging decentralized identifiers (DIDs) that allow users to control their identities across multiple services. As trends like the increased use of DIDs and AI-driven verification emerge, they promise to create a more connected and user-friendly digital identity realm.
The Role of Zero-Knowledge Proofs in Securing
Zero-knowledge proofs (ZKPs) are an innovative cryptographic method that enables one party (the prover) to convince another party (the verifier) that they possess certain information or can perform specific computations without disclosing any details about that information. This characteristic makes ZKPs highly effective for enhancing identity security while preserving user privacy.
Applications of ZKPs in Identity Management
- Credential Verification: ZKPs can validate credentials, such as educational degrees or licenses, without revealing sensitive details about the individual.
- Authentication: Users can authenticate their Identity using ZKPs, proving who they are without exposing passwords or private keys.
- Privacy-Preserving Data Sharing: ZKPs facilitate the secure data exchange, allowing entities like healthcare providers to verify a patient’s treatment eligibility without disclosing their entire medical history.
- Anonymous Credentials: ZKPs can create credentials that will enable access to services without revealing the user’s Identity.
Conclusion
In summary, AI-powered blockchain platforms represent the future of digital identity management. By combining blockchain security with AI’s intelligence, these platforms offer a more secure, efficient, and user-friendly way to manage digital identities. With applications across various industries and the potential to enhance user privacy and control, AI-powered blockchain solutions are set to revolutionize how we handle Identity in the digital age.
FAQs
How to Create a Digital Identity in Blockchain
Select a suitable blockchain platform like Ethereum or Hyperledger to create a digital identity in blockchain. Next, generate a digital wallet that produces a public-private key pair; the public key serves as your identity address. Create your identity profile by entering personal information into a smart contract on the blockchain, ensuring it’s encrypted for privacy. Finally, verify your Identity through trusted sources, recording this verification on the blockchain to enhance credibility.
Four Forms of Digital Identity
Digital Identity can be categorized into four forms:
- Static Identity includes unchanging identifiers like names and ID numbers.
- Dynamic Identity encompasses information that evolves, such as social media profiles.
- Biometric Identity involves unique physical traits like fingerprints and facial recognition.
- Attribute-based identity relies on specific claims or attributes, like professional credentials.
How to Create a Digital Signature in Blockchain
Creating a digital signature in blockchain involves a few key steps:
- Generate a public-private key pair using cryptographic algorithms.
- Create a hash of the message or transaction you wish to sign. Use your private key to sign this hash, resulting in a digital signature.
- The digital signature is attached to the transaction and stored on the blockchain for verification.
What is Proof of AI Blockchain?
Proof of AI blockchain is a consensus mechanism that combines artificial intelligence with blockchain technology. It validates transactions or data inputs using AI algorithms to analyze and verify information. This approach enhances decision-making, improves security, and optimizes resource allocation, all while maintaining transparency and trust in decentralized applications.