The digital world is on the brink of a significant shift, driven by the advancements in quantum computing. Unlike traditional computers that process information in binary bits (0s and 1s), quantum computers operate using qubits, which can exist in multiple states simultaneously. This parallel processing capability opens the door to solving complex problems at incredible speeds. While this development promises breakthroughs across many industries, one area of critical concern is cryptography, the cornerstone of security for systems like blockchain.
Blockchain technology, known for its decentralized nature and robust security via cryptographic techniques, is widely used in applications ranging from cryptocurrencies to supply chain management. However, the potential of quantum computing to break traditional encryption methods poses an imminent risk to blockchain’s integrity. This challenge necessitates the development of quantum-resistant cryptographic methods that can safeguard blockchain in a quantum-powered future.
The Impact of Quantum Computing on Blockchain Security
Blockchain’s security relies heavily on cryptographic methods such as RSA and Elliptic Curve Cryptography (ECC). These systems depend on mathematical problems that are extremely difficult for classical computers to solve within a reasonable timeframe. However, quantum computers can leverage Shor’s algorithm to solve these problems, rendering RSA and ECC vulnerable quickly. This means that a sufficiently powerful quantum computer could decrypt blockchain data, exposing sensitive information or altering transactions, which could undermine the entire premise of blockchain’s immutability and security.In light of this, the need to develop quantum-resistant cryptography has become urgent to ensure that blockchain networks remain secure even as quantum technology advances.
Quantum-Resistant Cryptography
As quantum computing continues to evolve, its ability to break conventional cryptographic algorithms presents a significant risk to digital security. Quantum-resistant cryptography (QRC), or post-quantum cryptography (PQC), focuses on creating secure cryptographic methods even in the presence of quantum computing capabilities.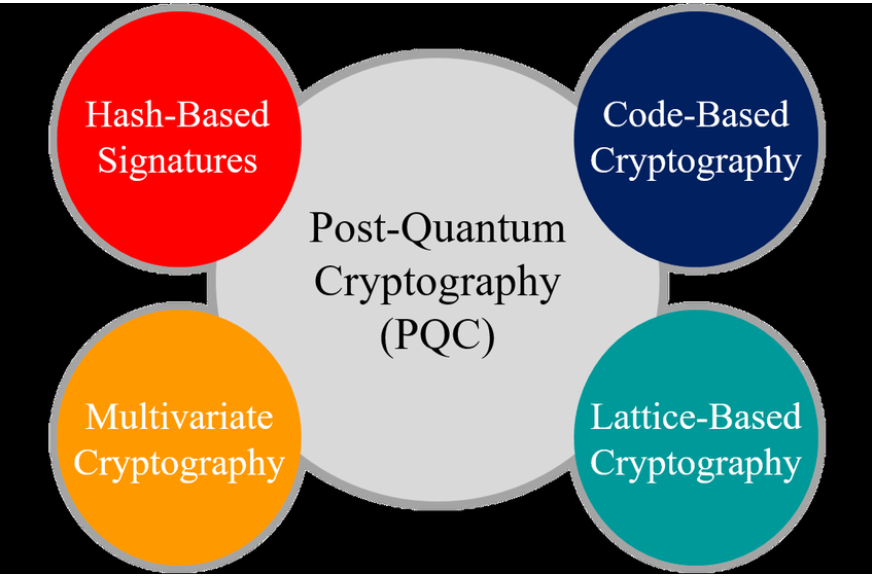
Core Features of Quantum-Resistant Cryptography
- Quantum Resilience: QRC algorithms are designed to resist quantum attacks like Shor’s algorithm, which can break current public-key encryption.
- Efficiency: Practical applications require QRC algorithms to be efficient enough to function in real-world systems without excessive computational overhead.
- Robust Security: These algorithms must match or surpass the security offered by traditional cryptography, ensuring long-term protection.
Major Types of QRC Algorithms
- Lattice-Based Cryptography: This class relies on the difficulty of specific problems involving lattices in high-dimensional spaces, with examples including NTRU, LWE, and Ring-LWE.
- Code-Based Cryptography: Based on error-correcting codes, this type uses the challenge of decoding specific types of codes. McEliece cryptosystem and Goppa codes are key examples.
- Hash-Based Cryptography: This approach utilizes cryptographic hash functions to help construct secure digital signatures and key exchange protocols, such as XMSS and SPHINCS.
- Supersingular Isogeny Cryptography (SIKE): A more recent method, SIKE is rooted in elliptic curve theory. It uses supersingular isogenies to create quantum-resistant public-key systems.
Standardization Initiatives
Various organizations are driving standardization efforts to ensure consistent and reliable adoption. The U.S. National Institute of Standards and Technology (NIST) is spearheading a multi-year project to evaluate and select quantum-resistant algorithms for formal use to establish a global benchmark.
Why Traditional Cryptography is Vulnerable to Quantum Computing
The inherent weakness of traditional cryptographic systems in the face of quantum computing lies in their reliance on computational difficulty, which is a bottleneck for classical computers but not for quantum machines. Quantum algorithms, such as Shor’s algorithm, can efficiently solve problems like large number factorization (which underpins RSA) and the elliptic curve discrete logarithm (which supports ECC). As a result, quantum computing renders these cryptographic methods insecure, urging the need for quantum-resistant alternatives.
Quantum Threats to Blockchain
The rise of quantum computing introduces significant threats to blockchain security. One of the most pressing concerns is quantum computers’ ability to reverse cryptographic protections, potentially allowing attackers to alter or falsify blockchain transactions. Furthermore, there is a threat of “harvest now, decrypt later” attacks, where malicious actors intercept and store encrypted data now with the intention of decrypting it once quantum computing reaches the necessary capacity.These risks underscore the urgent need for quantum-resistant encryption to protect blockchain networks from future breaches.
Developing Quantum-Resistant Cryptography
In response to these emerging threats, significant research is dedicated to developing quantum-resistant cryptographic methods. These new methods resist classical and quantum attacks, ensuring that blockchain systems remain secure despite technological advancements.Quantum-resistant cryptography focuses on algorithms that rely on mathematical problems that quantum computers find difficult or impossible to solve. Several promising approaches include lattice-based, hash-based, code-based, and multivariate-quadratic cryptography. Each approach offers unique strengths, depending on the specific use case within blockchain systems.
Key Approaches in Quantum-Resistant Cryptographic Methods
There are four primary approaches to quantum-resistant cryptography that are currently under investigation:
- Lattice-Based Cryptography: This method relies on the hardness of solving problems within a lattice structure. Even quantum computers struggle with these complex geometrical problems, making this a strong candidate for future blockchain encryption.
- Hash-Based Cryptography: Hash functions are fundamental to blockchain, and hash-based cryptography leverages the difficulty quantum computers face in reversing these functions. These methods are considered robust for securing blockchain transactions.
- Code-Based Cryptography: This approach uses error-correcting codes to secure data. Code-based cryptographic methods have been studied for decades and are deemed quantum-resistant.
- Multivariate-Quadratic Cryptography: By solving systems of quadratic equations, multivariate-quadratic cryptography offers another promising quantum-resistant solution, though more research is required to refine this method.
AI’s Role in Developing Quantum-Resistant Algorithms
Artificial intelligence (AI) is becoming an essential asset in creating quantum-resistant algorithms (QRAs), which aim to secure cryptographic systems against the immense power of quantum computers. Here’s how AI is helping accelerate the development of these algorithms:
Discovering New Algorithms
- Automated Exploration: AI can systematically explore various mathematical structures, identifying potential QRA candidates much faster than manual methods.
- Optimizing Existing Algorithms: AI can fine-tune the parameters of QRAs using techniques like genetic algorithms and machine learning models to enhance their resistance to quantum attacks and improve efficiency.
Enhancing Security
- Weakness Detection: AI can examine QRAs to uncover hidden vulnerabilities that quantum computers could exploit.
- Simulating Quantum Attacks: AI enables researchers to stress-test QRAs by simulating quantum attack scenarios, revealing strengths and areas for improvement.
Improving Efficiency
- Performance Optimization: AI can streamline the implementation of QRAs, reducing computational costs and optimizing them for real-world applications.
- Hardware Design: AI-driven techniques can help design specialized hardware, such as processors tailored to execute quantum-resistant cryptography more efficiently.
Quantum Circuit Design
- Circuit Development: AI assists in designing and optimizing quantum circuits that implement QRA operations efficiently, ensuring faster and more reliable performance.
- Error Mitigation: Using AI to develop quantum error correction codes can minimise the impact of noise and computational errors in quantum circuits, making QRAs more robust.
Evaluating and Benchmarking
- Setting Performance Standards: AI can help create performance benchmarks for evaluating QRAs, ensuring they meet rigorous security and efficiency standards.
- Algorithm Comparison: AI can automate the comparison of various QRA candidates, analyzing their strengths and weaknesses to identify the most effective solutions.
Supporting Collaborative Research
- Human-AI Synergy: AI can complement human researchers by handling complex, repetitive tasks, allowing researchers to focus on more creative problem-solving.
- Facilitating Knowledge Exchange: AI can help manage vast amounts of research data, improving knowledge sharing and collaboration among cryptography experts globally.
AI-Driven Solutions for Scalability
AI can address many of the scalability challenges associated with quantum-resistant cryptography. By automating the testing of various cryptographic methods and suggesting improvements, AI helps optimize these algorithms for real-world applications. This ensures that quantum-resistant encryption can scale to meet the demands of large blockchain networks without compromising security or performance.
Use Cases for Quantum-Resistant Cryptography in Blockchain
As quantum computing advances, the need for quantum-resistant cryptography (QRC) in blockchain becomes crucial to safeguard systems. Here are key use cases:
Financial Security
- Digital Currencies: Protecting cryptocurrencies like Bitcoin from quantum attacks.
- Payments & Banking: Securing transactions and preventing fraud.
Supply Chain
- Product Verification: Ensuring authenticity and traceability across supply chains.
- Transparency: Enhancing trust by reducing counterfeit risks.
Healthcare
- Patient Data: Safeguarding electronic health records.
- Medical Supply Chain: Verifying the authenticity of medical supplies.
Government Systems
- Elections: Ensuring the integrity of voting systems.
- Identity Protection: Preventing identity theft and securing personal data.
DeFi
- Smart Contracts: Securing automated financial transactions.
- Tokenized Assets: Protecting tokenized digital assets from quantum risks.
Implementing QRC ensures blockchain systems remain secure and reliable against quantum threats.
Conclusion
As the quantum computing era approaches, blockchain developers must prepare for its inevitable security challenges. AI-enhanced quantum-resistant cryptography offers a clear path forward, ensuring that blockchain remains a secure, decentralized platform for digital transactions and beyond. The collaboration between AI and cryptography experts will be key in fortifying blockchain systems for the future, ensuring that they remain resistant to the evolving threats posed by quantum computing.
FAQS
Which cryptographic methods are used in blockchain technology?
- Hash Functions: Create unique fixed-size outputs for data integrity (e.g., SHA-256).
- Public-Key Cryptography: Secures transactions using a public-private key pair (e.g., ECC).
- Digital Signatures: Verify authenticity using private key signatures.
- Consensus Algorithms: Use cryptographic techniques for network validation (e.g., PoW, PoS).
What are the three main types of cryptographic algorithms?
- Symmetric-Key Cryptography: The same key is used for encryption and decryption (e.g., AES).
- Asymmetric-Key Cryptography: Uses public and private keys (e.g., RSA, ECC).
- Hash Functions: One-way functions for data integrity (e.g., SHA-256).
Which are the three different encryption methods?
- Symmetric Encryption: One key for encryption and decryption (e.g., AES).
- Asymmetric Encryption: Public key for encryption, private key for decryption (e.g., RSA).
- Hashing: One-way data conversion for integrity (e.g., SHA-256).
What is the difference between encryption and cryptography?
- Cryptography: The broader field of securing data, including encryption, hashing, and signatures.
- Encryption: A process within cryptography that converts data into a secure, unreadable form (ciphertext) and back with a key.