In an increasingly interconnected world, identity verification is crucial for security and trust in digital spaces. Traditional, centralized systems, while widely used, pose significant risks—especially with the rise of cyberattacks and data breaches. Decentralized identity verification, enhanced with artificial intelligence (AI), promises a future where individuals have greater control over their personal data, while ensuring security and privacy.
This guide dives deep into how AI tools are shaping decentralized identity verification and authentication development, providing insights into technologies, challenges, and best practices.
Understanding Decentralized Identity Verification
How Traditional Identity Systems Work
Traditional identity verification systems rely on central authorities like governments, banks, or corporations to issue, verify, and store personal information. In this centralized model, data is housed in a single location, making it vulnerable to large-scale breaches and unauthorized access.
Limitations of Centralized Identity Systems
- Vulnerability to Cyberattacks: Centralized databases are attractive targets for hackers.
- Lack of User Control: Individuals have little to no say over how their data is managed.
- Data Privacy Concerns: Centralized systems often gather more information than necessary, raising concerns about surveillance and misuse.
Why Decentralized Solutions are Critical for the Future
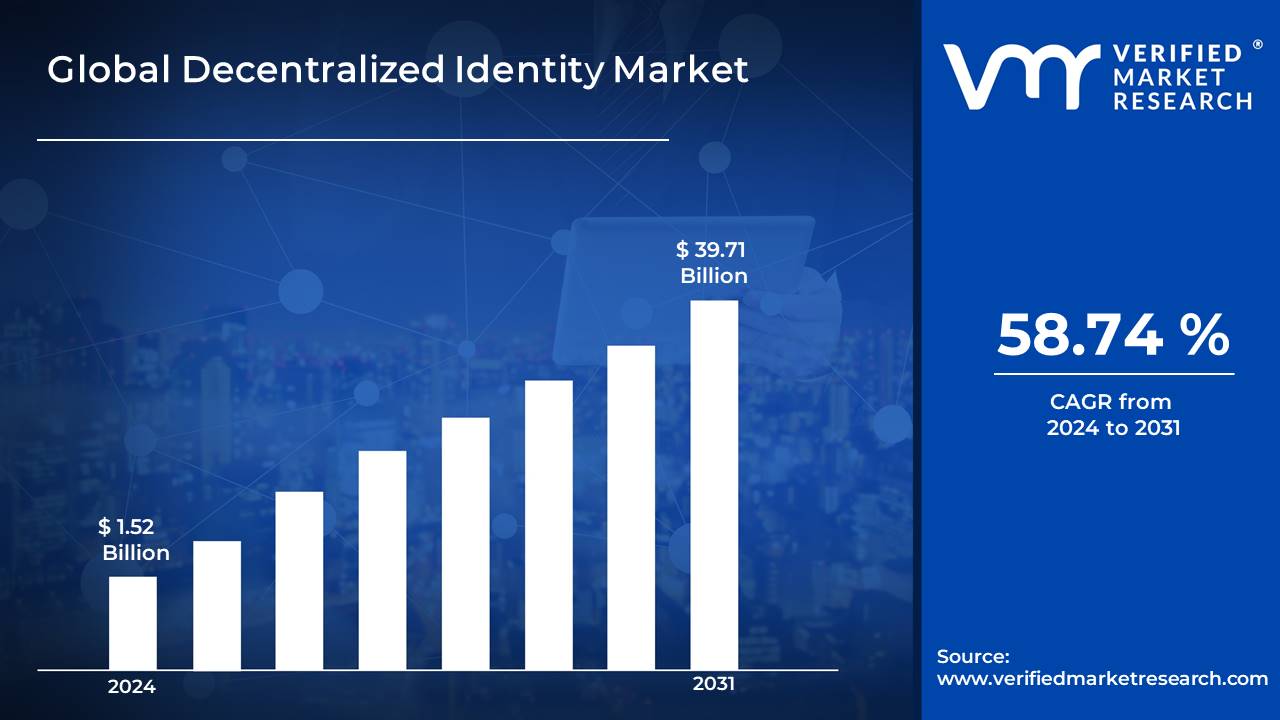
Think of decentralized identity like having a secure digital wallet that holds your personal details—things like your driver’s license or passport. But instead of relying on a government agency or company to keep this information, it’s stored across a network of computers, called a blockchain. Decentralized Identity Market size was estimated at USD 1.52 Billion in 2024 and is projected to reach USD 39.71 Billion by 2031, growing at a CAGR of 58.74% from 2024 to 2031.
Why is this approach better?
- Enhanced Security: Even if one computer in the network fails or is compromised, your data stays secure on the others.
- Greater Privacy: You decide who gets to access your information and when.
- More Independence: You’re not dependent on any single organization to manage or verify your identity.
How does it work?
When you need to prove who you are, you simply share a digital version of your ID from this wallet. The person or organization verifying your identity cross-checks it against the blockchain to ensure it’s authentic.
In summary, decentralized identity gives you control over your personal information, much like having your own personal vault for your digital identity.
AI’s Role in Strengthening Decentralized Verification Systems
AI can play a transformative role in boosting decentralized verification systems’ capabilities, security, and efficiency. Here’s how AI brings value to these systems:
Automation through Smart Contracts
-
- Streamlined Verification: AI automates the verification processes within smart contracts, enabling quick and accurate validation of identity claims and transactions.
- Enforcing Rules: By incorporating AI, smart contracts can implement complex, predefined rules and regulations, ensuring only authorized actions are performed and preventing fraudulent activities.
Boosting Data Privacy and Security
-
- Anomaly Detection: AI algorithms can detect irregular behaviours or patterns that signal potential data breaches or unauthorized access attempts, adding a protective layer to user data.
- Privacy-Preserving Techniques: AI helps integrate advanced privacy measures like homomorphic encryption or differential privacy, safeguarding sensitive user information while maintaining system integrity.
Improving Scalability and Efficiency
-
- Ledger Optimization: AI can enhance the performance of distributed ledgers by detecting bottlenecks and improving consensus algorithms for faster and more reliable network performance.
- Parallel Processing: With AI, decentralized systems can handle multiple verification tasks simultaneously, improving scalability and minimizing delays in data processing.
Fostering Interoperability
-
- Standardizing Protocols: AI aids in developing standard protocols for decentralized identity systems, ensuring that different platforms can seamlessly interact and verify identities across networks.
- Secure Data Exchange: AI enables secure and efficient data exchange between various decentralized networks, facilitating better communication and integration across systems.
Enhancing the User Experience
-
- Customized Verification: AI personalizes the verification process based on individual user behaviours and preferences, ensuring a smoother and more tailored experience.
- Simplified Interactions: AI streamlines and simplifies the interface, making decentralized systems more user-friendly and encouraging broader adoption.
Through the application of AI, decentralized verification systems can achieve higher levels of security, efficiency, and user engagement, addressing key challenges like scalability, privacy, and cross-platform interoperability.
Machine Learning Algorithms for Identity Authentication
Machine learning enhances identity authentication through various algorithms:
Support Vector Machines (SVMs)
- Binary Classification: Effective at distinguishing legitimate from fraudulent users.
- High-Dimensional Handling: Manages complex data with high-dimensional features.
Neural Networks
- Deep Learning: Utilizes architectures like CNNs and RNNs to learn complex patterns from large datasets.
- Biometrics: Excellent for facial and fingerprint recognition.
Random Forest
- Ensemble Learning: Combines multiple decision trees for better accuracy and reduced overfitting.
- Feature Insights: Reveals the importance of different features in authentication.
Bayesian Networks
- Probabilistic Modeling: Models uncertainties and adapts authentication based on variable relationships.
- Dynamic Policies: Adjusts to changing conditions and user behaviour.
Gradient Boosting Machines (GBMs)
- Iterative Learning: Builds models progressively to correct previous errors.
- Boosting: Enhances performance by combining weak learners into strong models.
Hidden Markov Models (HMMs)
- Sequential Data: Ideal for modelling sequences like typing patterns or voice data.
- Behavioural Biometrics: Authenticates based on user’s behavioural patterns.
Choosing the correct algorithm depends on the type of biometric data, accuracy needs, and computational resources. Often, combining algorithms results in more secure authentication systems.
AI’s Role in Enhancing Authentication Security
- Biometric Authentication: AI enhances facial, voice, and fingerprint recognition, ensuring precise identification even in challenging conditions.
- Behavioral Biometrics: AI can authenticate users based on their unique behaviours by analyzing typing patterns and walking gait.
- Anomaly Detection: AI identifies unusual login patterns and learns from past fraud cases to improve detection and prevent unauthorized access.
- Risk-Based Authentication: AI evaluates contextual factors such as location and device type to adjust security measures, dynamically balancing protection with user convenience.
- Passwordless Authentication: AI supports multi-factor authentication and enables secure, password-free logins through biometrics and other methods.
- Fraud Prevention: AI detects deepfakes and phishing attempts, safeguarding against sophisticated fraudulent tactics.
These AI-driven approaches make authentication systems more secure, efficient, and user-friendly, effectively tackling the complexities of modern security threats.
Building Trust in Decentralized AI Systems
Transparency in AI Algorithms
- Open-Source Models: Open-sourcing AI models allow users to examine the algorithms’ workings, enhancing trust by verifying fairness and reducing bias.
- Third-Party Audits: Independent audits ensure AI systems operate correctly and ethically, demonstrating accountability and deterring misuse.
Verifiable Credentials in Decentralized Networks
- Privacy-Preserving Verification: Users can validate their identity without disclosing extra personal data, crucial for privacy in decentralized environments.
- AI-Powered Management: AI streamlines the issuance and verification of credentials, minimizing errors and improving efficiency.
User Consent and Data Sovereignty
- Informed Consent: Clear information on data usage and consent ensures that users are aware of how their data is handled.
- Data Ownership and Sovereignty: Users retain control over their data, deciding how it’s used and stored, which helps prevent breaches and protects privacy.
Case Studies: AI in Decentralized Identity Verification
Sovrin Foundation
- Objective: To create a decentralized identity ecosystem that gives individuals control over their data.
- AI Utilization: Sovrin employs AI for credential verification, fraud detection, and the implementation of privacy-preserving methods.
- Outcome: Sovrin’s approach is poised to transform identity management, especially in sectors like healthcare and finance.
SelfKey
- Objective: To offer a decentralized platform for managing identities and accessing financial services.
- AI Utilization: SelfKey integrates AI for facial recognition, document validation, and risk assessment.
- Outcome: SelfKey enables individuals to manage their digital identities and access services without relying on intermediaries.
Civic
- Objective: To develop a decentralized platform that allows identity verification without disclosing personal details.
- AI Utilization: Civic uses AI for biometric verification, document authentication, and safeguarding privacy.
- Outcome: Civic’s platform can streamline identity verification across various sectors, including government and finance.
Conclusion
In an increasingly digital world, the shift from traditional, centralized identity systems to decentralized ones enhanced by artificial intelligence (AI) offers substantial benefits. Centralized systems are prone to data breaches and privacy issues, whereas decentralized systems provide greater control and security. AI enhances these systems by streamlining verification processes, improving biometric accuracy, and detecting anomalies.
Overall, AI-driven decentralized identity solutions promise enhanced security, privacy, and user control, setting the stage for a more secure digital future.
Developing AI Tools for Decentralized Systems with Codearies
At Codearies, we specialize in creating advanced AI tools tailored for decentralized systems. Our expertise in integrating artificial intelligence with blockchain technology transforms how businesses manage and secure digital operations. Feel free to reach out for a free consultation to discover how Codearies can revolutionize your decentralized systems with our cutting-edge AI tools.
Contact Us:
Email: contact@codearies.com
FAQs
How does AI affect digital identity?
AI enhances digital identity by automating verification processes, detecting anomalies, and personalizing security measures. It helps in efficiently managing identity data, preventing fraud through predictive analytics, and ensuring privacy with advanced encryption techniques. AI-driven systems make digital identity verification more secure, accurate, and user-friendly.
How do I get a Web3 ID?
To obtain a Web3 ID, you typically need to create an account on a Web3 platform that supports decentralized identities. This involves generating a digital wallet, verifying your identity through blockchain-based systems, and associating your personal information with a unique cryptographic key. Web3 IDs leverage decentralized networks to provide secure and user-controlled digital identities.
What is Web3 proof of identity?
Web3 proof of identity refers to using blockchain technology and decentralized systems to verify and manage digital identities. It involves using cryptographic methods to prove an identity’s authenticity without relying on central authorities. This ensures secure, transparent, and user-controlled verification of personal information in a decentralized environment.
What is KYC verification in blockchain?
KYC (Know Your Customer) verification in blockchain involves validating the identity of users through decentralized systems. It integrates blockchain technology to securely store and manage personal data, ensuring compliance with regulatory requirements while maintaining user privacy. Blockchain KYC uses smart contracts and cryptographic proofs to streamline and secure the verification process.